Search
Content type: Case Study
On 3 December 2015, four masked men in plainclothes arrested Isnina Musa Sheikh in broad daylight (at around 1 p.m.) as she served customers at her food kiosk in Mandera town, in the North East of Kenya, Human Rights Watch reported. The men didn’t identify themselves but they were carrying pistols and M16 assault rifles, commonly used by Kenyan defence forces and the cars that took her away had their insignia on the doors. Isnina’s body was discovered three days later in a shallow grave about…
Content type: Case Study
The prohibition against torture is absolute. There are no exceptional circumstances whatsoever which can be used to justify torture.
And yet, torture is still being carried out by state officials around the world, driven by states’ ability to surveil dissidents, and intercept their communications.
In 2007, French technology firm Amesys (a subsidiary of Bull) supplied sophisticated communications surveillance systems to the Libyan intelligence services. The systems allegedly permitted the…
Content type: Long Read
Over the coming months, PI is going to start to look a bit different. We will have a new logo and a whole new visual identity.
And in turn, our new visual identity will only be one step in a wider process of PI reconnecting with our core mission and communicating it more effectively to you, following on from extensive consultation with our staff, board, our supporters and our international partners.
Our current black ‘redacted’ Privacy International logo, and the austere Cold War era dossier…
Content type: News & Analysis
Updated January 18th 2021
The Government of Myanmar is pushing ahead with plans to require anyone buying a mobile SIM card to be fingerprinted and hand over their ID cards, according to procurement documents circulated to prospective bidders.
The plans are a serious threat to privacy in a country lacking any data protection or surveillance laws and where minorities are systematically persecuted, and must be scrapped.
According to technical requirements developed by Myanmar’s Post and…
Content type: Advocacy
This stakeholder report is a submission by Privacy International (PI), the National Coalition of Human Rights Defenders Kenya (NCHRD-K), The Kenya Legal & Ethical Issues Network on HIV and AIDS (KELIN), and Paradigm Initiative.
PI, NCHRD-K, KELIN, and Paradigm Initiative wish to bring their concerns about the protection and promotion of the right to privacy, and other rights and freedoms that privacy supports, for consideration in Kenya’s upcoming review at the 35th session of the Working…
Content type: Long Read
Following a series of FOI requests from Privacy International and other organisations, the Department of Health and Social Care has now released its contract with Amazon, regarding the use of NHS content by Alexa, Amazon’s virtual assistant. The content of the contract is to a big extent redacted, and we contest the Department of Health’s take on the notion of public interest.
Remember when in July this year the UK government announced a partnership with Amazon so that people would now…
Content type: News & Analysis
This creates a restraint on all people who merely seek to do as people everywhere do: to communicate freely.
This is a particularly worrying development as it builds an unreliable, pervasive, and unnecessary technology on top of an unnecessary and exclusionary SIM card registration policy. Forcing people to register to use communication technology eradicates the potential for anonymity of communications, enables pervasive tracking and communications surveillance.
Building facial recognition…
Content type: News & Analysis
On 24 October 2019, the Swedish government submitted a new draft proposal to give its law enforcement broad hacking powers. On 18 November 2019, the Legal Council (“Lagråd”), an advisory body assessing the constitutionality of laws, approved the draft proposal.
Privacy International believes that even where governments conduct hacking in connection with legitimate activities, such as gathering evidence in a criminal investigation, they may struggle to demonstrate that hacking as…
Content type: News & Analysis
In the last few months strong concerns have been raised in the UK about how police use of mobile phone extraction dissuades rape survivors from handing over their devices: according to a Cabinet Office report leaked to the Guardian, almost half of rape victims are dropping out of investigations even when a suspect has been identified. The length of time it takes to conduct extractions (with victims paying bills whilst the phone is with the police) and the volume of data obtained by the…
Content type: News & Analysis
*Photo by Michelle Ding on Unsplash
Pat Finucane was killed in Belfast in 1989. As he and his family ate Sunday dinner, loyalist paramilitaries broke in and shot Pat, a high profile solicitor, in front of his wife and children.
The Report of the Patrick Finucane Review in 2012 expressed “significant doubt as to whether Patrick Finucane would have been murdered by the UDA [Ulster Defence Association] had it not been for the different strands of involvement by the…
Content type: Long Read
Miguel Morachimo, Executive Director of Hiperderecho. Hiperderecho is a non-profit Peruvian organisation dedicated to facilitating public understanding and promoting respect for rights and freedoms in digital environments.The original version of this article was published in Spanish on Hiperderecho's website.Where does our feeling of insecurity come from? As we walk around our cities, we are being observed by security cameras most of the time. Our daily movement, call logs, and internet…
Content type: Long Read
*Photo by Kristina Flour on Unsplash
The British government needs to provide assurances that MI5’s secret policy does not authorise people to commit serious human rights violations or cover up of such crimes
Privacy International, along Reprieve, the Committee on the Administration of Justice, and the Pat Finucane Centre, is challenging the secret policy of MI5 to authorise or enable its so called “agents” (not MI5 officials) to commit crimes here in the UK.
So far we have discovered…
Content type: Advocacy
On November 1, 2019, we submitted evidence to an inquiry carried out by the Scottish Parliament into the use of Facial Recognition Technology (FRT) for policing purposes.
In our submissions, we noted that the rapid advances in the field of artificial intelligence and machine learning, and the deployment of new technologies that seek to analyse, identify, profile and predict, by police, have and will continue to have a seismic impact on the way society is policed.
The implications come not…
Content type: Long Read
Sitting on the ground inside an unadorned courtyard in Koira Tegui, one of Niamey’s most popular districts, Halimatou Hamadou shows a copy of what, she’s been told, is a certificate of birth.
The 33 year old woman, who’s unable to read and write, received it days earlier during a crowded public ceremony at a nearby primary school.
“It’s my first document ever,'' she says, with surprise.
Thanks to the paper, she’ll be able to take part in a crucial passage for the future of Niger: the…
Content type: Long Read
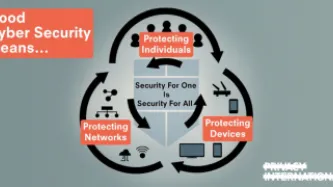
The pressing need to fix our cybersecurity (mis)understandings
Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being different concepts, the confusion between them and the broad application of criminal statutes is still leading to the criminalise legitimate behaviour.
All of this represents a sizable challenge…
Content type: News & Analysis
Picture: CC: BY (Kirill Sharkovski)-SA
This article was written by Jamila Venturini from Derechos Digitales. The original version (in Spanish) is available here.
How implementing social protection programmes that condition access to basic services to state and private surveillance exacerbate the prevailing inequality on the continent.
While the gap between rich and poor is increasing in the world, Latin America remains the most unequal region of the world. According to the Economic…
Content type: Press release
Tomorrow, the UN Special Rapporteur on extreme poverty and human rights will present his annual report to the UN General Assembly in New York on digital technology, social protection and human rights. On the same day, Privacy International will be launching its own series on surveillance in the provision of social services.
The Special Rapporteur warns that specific areas need to be addressed to "avoid stumbling zombie-like into a digital welfare dystopia" and that "values such as…
Content type: Long Read
This research is the result of a collaboration between Grace Tillyard, a doctoral researcher in the Media, Communications and Cultural Studies department at Goldsmiths College, London, and Privacy International.
Social Protection Systems in the Digital Age
In the digital age, governments across the world are building technologically integrated programmes to allow citizens to access welfare payments. While smart and digital technologies hold the potential to streamline administrative…
Content type: Long Read
[Photo credit: Images Money]
The global counter-terrorism agenda is driven by a group of powerful governments and industry with a vested political and economic interest in pushing for security solutions that increasingly rely on surveillance technologies at the expenses of human rights.
To facilitate the adoption of these measures, a plethora of bodies, groups and networks of governments and other interested private stakeholders develop norms, standards and ‘good practices’ which often end up…
Content type: Long Read
In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone…
Content type: News & Analysis
On 11 October 2019, Privacy International together with EDRi, BEUC, AccessNow and Open Society European Policy Institute, sent an open letter to EU Member States, to urge them to conclude the negotiations on the ePrivacy Regulation.
The letter highlights the urgent need for a strong ePrivacy Regulation in order to tackle the problems created by the commercial surveillance business models, and expresses the deep concerns by the fact that the Member States, represented in the Council of the…
Content type: Long Read
Photo by Nadine Shaabana on Unsplash
Digital identity providers
Around the world, we are seeing the growth of digital IDs, and companies looking to offer ways for people to prove their identity online and off. The UK is no exception; indeed, the trade body for the UK tech industry is calling for the development of a “digital identity ecosystem”, with private companies providing a key role. Having a role for private companies in this sector is not necessarily a problem: after all, …
Content type: News & Analysis
A new UK Times report claims that “WhatsApp, Facebook and other social media platforms will be forced to disclose encrypted messages from suspected terrorists, paedophiles and other serious criminals under a new treaty between the UK and the US.”
Several other media outlets have followed up on the report, with headlines such as “UK and US set to sign treaty allowing UK police ‘back door’ access to WhatsApp and other ‘end to end encrypted’ messaging platforms”.
While the…
Content type: Long Read
Content type: Advocacy
Earlier this year, the UN Special Rapporteur on freedom of expression called for an “immediate moratorium on the global sale and transfer of private surveillance technology”, warning that “unlawful surveillance continues without evident constraint”, is leading to arbitrary detention, torture and possibly to extrajudicial killings. Without urgent action, there is every reason to believe that the situation will only get worse for people around the world. At Privacy…
Content type: News & Analysis
Photo: The European Union
“Border Externalisation”, the transfer of border controls to foreign countries, has in the last few years become the main instrument through which the European Union seeks to stop migratory flows to Europe. Similar to the strategy being implemented under Trump’s administration, it relies on utilising modern technology, training, and equipping authorities in third countries to export the border far beyond its shores.
It is enabled by the adoption…
Content type: News & Analysis
Photo by Francesco Bellina
The wars on terror and migration have seen international funders sponsoring numerous border control missions across the Sahel region of Africa. Many of these rely on funds supposed to be reserved for development aid and lack vital transparency safeguards. In the first of a series, freelance journalist Giacomo Zandonini sets the scene from Niger.
Surrounded by a straw-yellow stretch of sand, the immense base of the border control mobile company of Maradi, in southern…
Content type: Long Read
Photo: Francesco Bellina
Driven by the need to never again allow organised mass murder of the type inflicted during the Second World War, the European Union has brought its citizens unprecedented levels of peace underpinned by fundamental rights and freedoms.
It plays an instrumental role in protecting people’s privacy around the world; its data protection regulation sets the bar globally, while its courts have been at the forefront of challenges to unlawful government surveillance…
Content type: News & Analysis
Today, the High Court of South Africa in Pretoria in a historic decision declared that bulk interception by the South African National Communications Centre is unlawful and invalid.
The judgment is a powerful rejection of years of secret and unchecked surveillance by South African authorities against millions of people - irrespective of whether they reside in South Africa.
The case was brought by two applicants, the amaBhungane Centre for Investigative Journalism and journalist Stephen…
Content type: Examples
Bethany Christian Services, an international pregnancy support and adoption agency, is launching a programme with Copley Advertising to send targeted ads to individuals visiting Planned Parenthood clinics, abortion clinics, methadone clinics and high-risk areas (AHPA). The targeting will be done through the use of geo fencing based on smartphones located within the selected locations.
Source: https://www.liveaction.org/news//adoption-agency-send-pro-life-ads-smartphones-inside-abortion-…