Search
Content type: Long Read
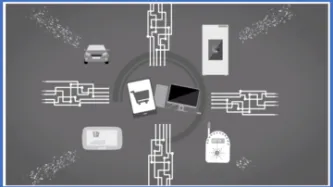
Everyday objects and devices that can connect to the Internet -- known as the Internet of Things (IoT) or connected devices -- play an increasing role in crime scenes and are a target for law enforcement. Exploiting new technologies that are in our homes and on our bodies as part of criminal investigations and for use as evidence, raises new challenges and risks that have not been sufficiently explored.
We believe that a discussion on the exploitation of IoT by law enforcement would…
Content type: News & Analysis
It's a big question, have you purchased a card for your local surveillance camera on Surveillance Camera Day?
Yes, Surveillance Camera Day is a real thing and happens on 20 June.
Perhaps your local community could create a bingo card to see who knows where all the local cameras are. Are there any on your local bins, how about the lampposts or a billboard?
Have you had a facial recognition van in your local community? Did you see the police helicopter crew video camera…
Content type: Examples
As part of its planning for the 2020 Olympic Games, due to be held in Tokyo, Japan approved a law that would allow the government to conduct a survey to identify vulnerable Internet of Things devices. The National Institute of Information and Communications Technology staff who carry out the survey, who will be supervised by the Ministry of Internal Affairs and Communications, are required to follow strict rules in attempting to hack into these devices: they are only allowed to use default…
Content type: Long Read
The UK border authority is using money ring-fenced for aid to train, finance, and provide equipment to foreign border control agencies in a bid to “export the border” to countries around the world.
Under the UK Border Force’s “Project Hunter”, the agency works with foreign security authorities to bolster their “border intelligence and targeting” capabilities with UK know-how and equipment.
As well as the provision of equipment and training, the Border Force is also advising countries on…
Content type: State of Privacy
Table of contents
Introduction
Right to Privacy
Communication Surveillance
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgement
The State of Privacy in Colombia is the result of an ongoing collaboration by Privacy International and Fundación Karisma and Dejusticia.
Key Privacy Facts
1. Constitutional privacy protection: The constitution contains an explicit protection of the right to privacy (Article 15 of the 1991 constitution).
2…
Content type: State of Privacy
Table of contents
Introduction
Right to Privacy
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgment
The State of Privacy in Pakistan is the result of an ongoing collaboration by Privacy International and the Digital Rights Foundation.
Between 2014-2016, Bytes for All contributed to previous versions of the 'Data Protection' sections of this briefing.
Key Privacy Facts
1. Constitutional privacy protections: Article 14(1) of…
Content type: State of Privacy
Table of contents
Introduction
Right to Privacy
Communication Surveillance
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgement
The State of Privacy in India is the result of an ongoing collaboration by Privacy International and the Centre for Internet & Society.
Key Privacy Facts
1. Constitutional privacy protections: In 2017, the Indian Supreme Court ruled that the Indian constitution guarantees a right to privacy.
2. Data…
Content type: Examples
In May 2018, UK-based security researcher Robert Wiggins discovered that the mobile app TeenSafe, marketed as a secure app for iOS and Android, was storing data it collected on servers hosted on Amazon's cloud without a password and openly accessible. The app lets parents monitor their children's text messages, location, browsing history, and apps, as well as who they called and when, and does not require parents to obtain their children's consent. The insecurely stored 10,200 records included…
Content type: Long Read
It’s 15:10 pm on April 18, 2018. I’m in the Privacy International office, reading a news story on the use of facial recognition in Thailand. On April 20, at 21:10, I clicked on a CNN Money Exclusive on my phone. At 11:45 on May 11, 2018, I read a story on USA Today about Facebook knowing when teen users are feeling insecure.
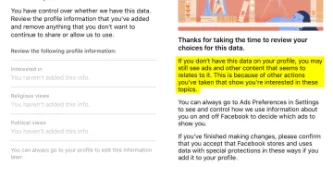
How do I know all of this? Because I asked an advertising company called Quantcast for all of the data they have about me.
Most people will have never heard of…
Content type: Long Read
The Sustainable Development Goals (SDGs) are the United Nations-led initiative to define the development agenda. Building on the eight Millennium Development Goals, the SDG’s 17 goals – and the 169 targets – serve as an opportunity to tackle many of the most pressing issues in the world today. The SDGs are also explicitly grounded in human rights. Goal 16 on “peace, justice, and sustainable institutions” aims to “Promote peaceful and inclusive societies for sustainable development, provide…
Content type: Long Read
Privacy International’s new report shows how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies. Driven by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, peoples’ rights, and the rule of law.To ensure that surveillance powers used by governments are used to protect rather than endanger people, it is essential that the public,…
Content type: Report
Countries with powerful security agencies are spending literally billions to equip, finance and train security and surveillance agencies around the world — including authoritarian regimes. This is resulting in entrenched authoritarianism, further facilitation of abuse against people, and diversion of resources from long-term development programmes.
Privacy International's report 'Teach 'em to Phish: State Sponsors of Surveillance' examines this problem closely, providng examples from US, China…
Content type: Long Read
Privacy International (PI) has today released a new report, 'Teach 'em to Phish: State Sponsors of Surveillance', showing how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies.
Spurred by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, rights, and the rule of law.
As well as providing a background to the issue, the report…
Content type: Press release
Privacy International has today released a report that looks at how powerful governments are financing, training and equipping countries — including authoritarian regimes — with surveillance capabilities. The report warns that rather than increasing security, this is entrenching authoritarianism.Countries with powerful security agencies are spending literally billions to equip, finance, and train security and surveillance agencies around the world — including authoritarian regimes. This is…
Content type: Long Read
This piece was written by PI voluteer Natalie Chyi.
Transparency is necessary to ensure that those in power – including governments and companies – are not able to operate in the dark, away from publicscrutiny. That’s why calls for more transparency are routine by everyone from civil society and journalists to politicians.
The bigger picture is often lost when transparency is posed as the only solution to shadowy state and corporate powers. For one, the term is so broadly understood that it…
Content type: Advocacy
Privacy and security are both essential to protecting individuals, including their autonomy and dignity. Undermining privacy undermines the security of individuals, their devices and the broader infrastructure. People need privacy to freely secure themselves, their information, and fully enjoy other rights.
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. When governments hack for surveillance purposes, they seek to…
Content type: News & Analysis
This piece originally appeared here.
We are much more than our physical selves. We are also digital. Every moment we generate more data. Although sometimes this data is under our control, increasingly it is not. This uncontrolled data—this metadata—is often generated as a result of our interactions, movements, sentiments, and even our inaction. Despite being beyond our control, our metadata is still accessible to many. Hardly a day goes by without a news story or global event involving data: a…
Content type: Advocacy
Introduction
Why We Are So Concerned about Government Hacking for Surveillance
Scope of Our Safeguards
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4. Judicial Authorisation
5. Integrity of information
6. Notification
7. Destruction and Return of Data
8. Oversight and Transparency
9. Extraterritoriality
10. Effective Remedy
Commentary on each
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4.…
Content type: Examples
At the 2016 Usenix Workshop on Offensive Technologies, researchers from the University of Michigan presented the results of tests that showed that industrial vehicles - a 2006 semi-trailer and a 2001 school bus - were subject to the same security flaws as had already been found in domestic cars. Via digital signals sent within a big truck's internal network, the researchers were able to change the truck's instrument panel readout, trigger unintended acceleration, and even disable part of the…
Content type: Key Resources
Introduction
Why We Are So Concerned about Government Hacking for Surveillance
Scope of Our Safeguards
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4. Judicial Authorisation
5. Integrity of information
6. Notification
7. Destruction and Return of Data
8. Oversight and Transparency
9. Extraterritoriality
10. Effective Remedy
Commentary on each
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4.…
Content type: Long Read
Introduction
Why We Are So Concerned about Government Hacking for Surveillance
Scope of Our Safeguards
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4. Judicial Authorisation
5. Integrity of information
6. Notification
7. Destruction and Return of Data
8. Oversight and Transparency
9. Extraterritoriality
10. Effective Remedy
Commentary on each
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4.…
Content type: Examples
Facebook has come under fire after leaked documents revealed the social media site has been targeting potentially vulnerable children.
The allegations suggest the company is gathering information on young people who “need a confidence boost” to facilitate predatory advertising practices.
Confidential documents obtained by The Australian reportedly show how Facebook can exploit the moods and insecurities of teenagers using the platform for the benefit of advertisers.…
Content type: Case Study
Invisible and insecure infrastructure is facilitating data exploitation
Many technologies, including those that are critical to our day-to-day lives do not protect our privacy or security. One reason for this is that the standards which govern our modern internet infrastructure do not prioritise security which is imperative to protect privacy.
What happened?
An example of this is Wi-Fi, which is now on its sixth major revision (802.11ad). Wi-Fi was always designed to be a verbose in…
Content type: News & Analysis
7 July 2017
War profiteers are finding the data business easy going. The have wielded their unwarranted influence and applied their business model of causing and then profiting from insecurity and applied it to the digital age; the results have been more profit for them and less liberty for you.
When a politician riles against an evil tech giant for providing ‘safe spaces’ online, it’s a political distraction. The real battle for your data is being fought between the emergent tech…
Content type: News & Analysis
There are three good reasons why security is so hard for NGOs. First, we are afraid to speak about meaningful security. Second, we focus on the wrong areas of security and in turn spend money and prioritise the wrong things. Third, we struggle to separate the world we want from the worlds we build within our own organisations. At PI we have failed and struggled with each of these for over 20 years. Out of exhaustion, we decided to do something about it: we are building an open framework, a…
Content type: News & Analysis
Surveillance in digital spaces is the policing and monitoring of activity of those occupying these spaces. Surveillance affects free speech, privacy and behaviour of digital users. Feminism and a feminist approach to surveillance puts marginalised communities, those that are victims of class discrimination, racial and patriarchal structures, at the centre of discourse around privacy and surveillance.
Surveillance in Pakistan is often seen as an issue of national security. With the National…
Content type: News & Analysis
The short answer is yes.
I'm sure many of you have seen people with stickers over their webcams and wondered why (probably writing that person off as paranoid). But it's well known in tech circles that a camera in a computer or smartphone can be turned on remotely by an attacker with the resources, time, and motivation.
Security is hard, and our defences are weak. The capability of an adversary to attack your devices doesn't necessarily hinge upon a consumer choice of…
Content type: Press release
On 5 October 2017, Privacy International will appear before the UK Court of Appeal to continue its challenge to the British government's large scale hacking powers. The case questions the decision by the Investigatory Powers Tribunal (IPT) to sanction the UK government's power to hack broad categories of people or property without any individualised suspicion.
TIMELINE AND KEY POINTS
- Privacy International began fighting bulk government hacking in 2014 at the…
Content type: Case Study
For those concerned by reporting of Facebook’s exploitation of user data to generate sensitive insights into its users, it is worth taking note of WeChat, a Chinese super-app whose success has made it the envy of Western technology giants, including Facebook. WeChat has more than 900 million users. It serves as a portal for nearly every variety of connected activity in China. Approximately 30% of all time Chinese users spend on the mobile internet centers around…
Content type: Long Read
This piece was originally published in Lawfare in July 2017.
The United Kingdom has been a key partner in the United States’ efforts to reform the process that law enforcement officials use to make cross-border requests for data. These efforts address both foreign governments’ requests for data stored in the U.S. and reciprocal requests by the U.S. government for data stored abroad. As part of these efforts, the U.S. and the U.K. have negotiated a draft bilateral agreement (“U…